ACTIVE CAMPAIGN
Plala, a major Japanese Internet service provider, is currently the target of an extensive phishing campaign. The phishing sites typically serve a fraudulent Plala login portal to the prospective victim, prompting them to enter a username and password:
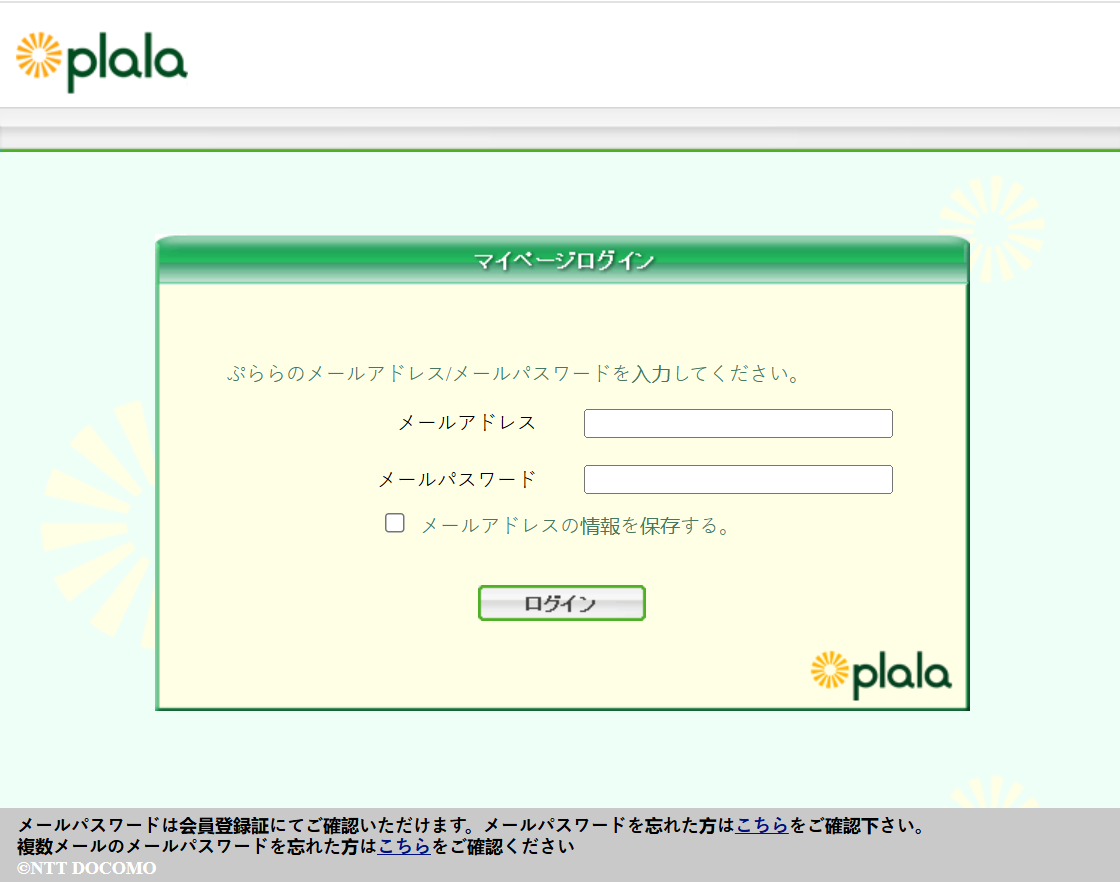
Indicators of Compromise
The structure of nearly every Plala phishing page is almost identical, despite them spanning over a range of disparate domains.
The following are common attributes between all the pages:
- The title of the page is ぷらら Webメール
- Comments
- ========= HEADER =========
- ========= CAUTION =========
- ========= CONTENTS =========
- ========= FOOTER =========
- The phishing page itself is generally hosted within a */Sites/ subdirectory
- Victim credentials are exfiltrated via a POST request to
- {MALICIOUS_DOMAIN}/Sites/cgi-binsso/pf/agent_sso[.]php
- 0be823c43133470e457a8066e02ef661adbe9b3d08e43a11ebeda87562fe361b
- 21d54f5ec6de68b434702976a05f547e47c1a7435c581ff8e8607235b6694221
- 34e87afc825b9f62cdfcc89db23898dfe09151904bca4debdb9aaef7d2cc4dcb
- 4e6fff51beaec33a7639e509aa82466c31cabfdf23ea24850edb76d873596b8c
- 548f2d6f4d0d820c6c5ffbeffcbd7f0e73193e2932eefe542accc84762deec87
- 5879f5c218c342a06b8eccf5376bdc944d99167de692ceff87324dcffa388778
- 662a02c554ce83d623a3f8b01a1fc02ad7238798d2207ac839f8d129ab3decdd
- 9505b2b5f3b5448531627cac0b769965be26d60c4bd64976295c058f2704243a
- 95518cbec0d55a574a9c8ef72a2a7d62ac0d40a4de5dfe67a76a7d214dc8b743
- 95c95e30e1bcb7532e7be902b3bd07fc01f8c38ca0bd3c590c8e4c0a11bcbc74
- abac16ca16c7dd5ed2d0c3c53b6ea53474224de2ebe6d546e860b73df5334f54
- ba71589b6bb729587c3c110462cf7843859a61d03b0f9bb6c9724cf40cdd9f76
- e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
- ec2716d4c90cf8b58b22978f562c937382d76f259fbd5a82b2738ab6ccba0b51
Mapping Out the Campaign
The phishing campaign appears to rely on both compromising vulnerable websites and purchasing domains as a means of facilitating the campaign’s infrastructure.
To determine the extent of the campaign, we used PhishTank’s (PT) database of submitted phishing domains. Scanning purely for domains with the keyword “plala”, we can observe over 30 malicious/compromised domains. Some recent examples include:
- hxxps[://]43cr[.]com/plala-account
- hxxps[://]arntours[.]com/plalawebmail/Sites/index[.]html
- hxxps[://]jnintllc[.]com//plala[.]web[.]jp/Sites/index[.]html
- hxxps[://]hupp234[.]com/plalawebmail/Sites/index[.]html
- hxxps[://]ruchitadesigncompany[.]com/plala[.]web001/Sites/index[.]html
with the earliest recorded instance of a Plala campaign domain appearing in the PT database on June 6th of 2025.
If we expand our definition to include the frequently used /Sites/index.html filepath, there are over 80 malicious/compromised domains. Examples of these include:
- hxxps[://]srikrishnahardwares[.]com/MentorAccount/Sites/index[.]html
- hxxps[://]turnkeyhosting[.]com//CHECKINGACCONT2035/Sites/index[.]html
- hxxps[://]alwalaemfood[.]com/pl/Sites/index[.]html
- hxxps[://]xetadesigns[.]com//ACCOUNTUPDATE2025/Sites/index[.]html
- hxxps[://]arntours[.]com/plalawebmail/Sites/index[.]html
- https://hongkonginternationalhomewarescoltd.com/yoursafety/Sites/index.html
- hxxps[://]i-care[.]one/Softaccount/Sites/index[.]html
Here, the earliest known Plala campaign domain appears in the PT database on May 21st of 2025.
Still yet, domains such as
- hxxps[://]netfibratelecomunicacoes[.]com[.]br/admin-index/webmail_login[.]php
- hxxps[://]ploplae220[.]com/cgi-bin/update1/
host Plala campaign pages without adhering to either of the mentioned patterns.
Malicious sites continue to roll out on a regular basis – on 8/31/25 and 9/1/25 alone, nearly a dozen confirmed Plala campaign sites were submitted to the PT database.
If you have any additional information or artifacts that pertain to the Plala phishing campaign, please contact us at cybersecurenotif@proton.me.
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣤⣶⣶⣶⠿⡿⢶⣶⣶⣶⣤⣄⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣠⡄⠀⠀⠀⢀⣠⣴⣿⠿⠛⠉⠁⠀⠀⠀⠀⠀⠀⠉⠙⠻⢿⣷⣦⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠰⣿⣿⣷⣶⣶⣿⠟⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠻⣿⣧⡉⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢿⣿⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⢻⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢿⣿⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣾⡿⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⠀⠀⠀⠈⢿⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⠇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣸⣿⣿⣿⡄⠀⢀⣾⣿⣧⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⠻⡿⠛⠁⢀⣾⣿⡛⣿⣿⣶⣤⣤⣤⣶⣿⣦ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⣾⣿⠟⠰⢠⢉⠹⡙⢋⠹⣩⣿⣿ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣴⣿⡿⢛⠡⢊⡑⠢⢌⠢⡑⢌⣲⣿⣿⠋ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⢿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣦⣅⣊⡔⣨⢱⣌⣦⣽⣿⡿⠛⠁⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠻⣿⣦⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣹⣿⡿⠿⠿⠿⠿⠟⠛⠋⠁⠀⠀⠀⠀ ⣠⣤⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣀⣀⣹⣿⣿⣶⣤⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢰⣿⣏⡁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⣿⣿⣿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣠⣶⣿⣿⣿⣿⣿⠿⠿⠿⢿⣿⠏⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠸⣿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⣿⣿⡍⠻⣿⣶⣄⡀⠀⠀⣀⣠⣴⣾⣿⠿⠟⠛⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠿⣿⣦⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⣿⣿⣿⣦⡀⠙⠻⠿⢿⣿⠿⠛⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣤⣤⣤⣤⣤⣤⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⢿⣿⣆⠀⠀⠀⠀⠀⠀⠀⠀ ⠿⣿⡍⠻⣿⣦⣄⠀⠀⠁⠀⠀⢀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣀⣴⣶⣿⠿⠟⠛⠉⠋⠛⠛⠿⣿⣶⣄⠀⠀⠀⠀⠀⠀⠀⠀⠹⣿⣦⠀⠀⠀⠀⠀⠀⠀ ⠀⣿⣷⡀⠈⠛⢿⡿⠂⠀⠀⠀⢸⣿⣿⣿⣷⣶⣶⣶⣿⣿⣿⡿⠟⠛⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣦⠀⠀⠀⠀⠀⠀⠀⠀⠹⣿⡆⠀⠀⠀⠀⠀⠀ ⠀⠸⣿⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⣄⡀⠈⠁⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⣇⠀⠀⠀⠀⠀⠀⠀⠀⣿⣇⠀⠀⠀⠀⠀⠀ ⠀⠀⢸⣿⣇⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⣿⢿⣿⣿⣿⣿⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣻⣿⡄⠀⠀⠀⠀⠀⠀⠀⣹⣯⠀⠀⠀⠀⠀⠀ ⠀⠀⠈⢿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⡏⠇⠀⠀⠀⠀⠀⠀⠀⣽⡷⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠈⣿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠹⣿⣿⣿⣿⣿⣿⠇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣾⡿⠃⠀⠀⠀⠀⠀⠀⠀⢀⣿⡇⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠹⣿⣧⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣶⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⣾⣿⠟⠁⠀⠀⠀⠀⠀⠀⠀⢀⣾⣿⠇⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠘⢿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⠻⢿⣿⣶⣶⣤⣤⣤⣤⣤⣶⣶⣿⡿⠟⠋⠁⠀⠀⠀⠀⠀⠀⠀⠀⣠⣿⡿⠃⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠈⠛⣿⣷⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠉⠉⠉⠉⠉⠉⠉⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⣠⣴⣿⡿⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⠻⢿⣷⣦⣤⣄⣀⣀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣀⣀⣤⣴⣶⣿⡿⠿⠛⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠉⠙⠛⠛⠿⠿⠿⠿⢿⡿⣿⣿⣿⢿⣿⡿⣿⡿⣿⢿⠿⠿⠿⠛⠛⠛⠋⠉⠁⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀

 (C:)
(C:) phishing campaigns
phishing campaigns Plala
Plala