- As of 7/6/2025, there are currently
1280 variations of the https://portal.gov{two_letters}.top/inbmv domain that are all live and operational.
This scam site requires you to interact with it via a mobile device; however, if your preferred research environment is a desktop computer or laptop, you may also use User-Agent switching functionalities built into browsers such as Google Chrome.
Any interaction with sites using SumKit inherently carries a high level of risk and should not be done without proper safeguards and preparation. SqueakyFlotilla highly cautions against interacting with these sites, and are not liable for compromised information or incurred damages should others seek to experiment with the site.
SumKit
A new strain of phishing kit has entered the market – one with a consistent mispelling littered throughout its code:
sendData({
"type": "sumbit_card",
"arg": arg
});
...
sendData({
"type": "sumbit_code",
"arg": {
"code": code
}
});
in lieu of this pattern, we’ve decided to give the moniker of SumKit to this new template.
Overview
SumKit is a phishing template that follows in the stead of a bulk of its predecessors, warning victims of a supposed toll payment violation. When navigated to on a mobile device, the site purports to be a Bureau of Motor Vehicles portal and asks for basic victim info (name, address, etc.) along with their credit card information.
What the Victim Sees
Site Functionalities
Tokens
When the victim clicks onto the first page of the site, SumKit reaches out to the endpoint
{BASE_URL}/front/check.ip?token=123
in order to retrieve a token which will be assigned to the victim. The token is only returned under the condition that the connecting browser’s user agent is indicative of a mobile device, and is formatted as follows:
{
"code":"succeed",
"data":
{
"cardVerify":true,
"encryption":true,
"isTips":false,
"token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6IjY5MTA5MTg1OTUwMTA2MSJ9.EvByTF9Pdo-vq1mLaMe2B2617yF8oSsQlsLK70lK-M0",
"succeed":false
}
}
Baking Information Into Cookies
In order to exfiltrate victim data, SumKit encodes any entered information into Base64 and stores the result in a variety of cookies. Namely:
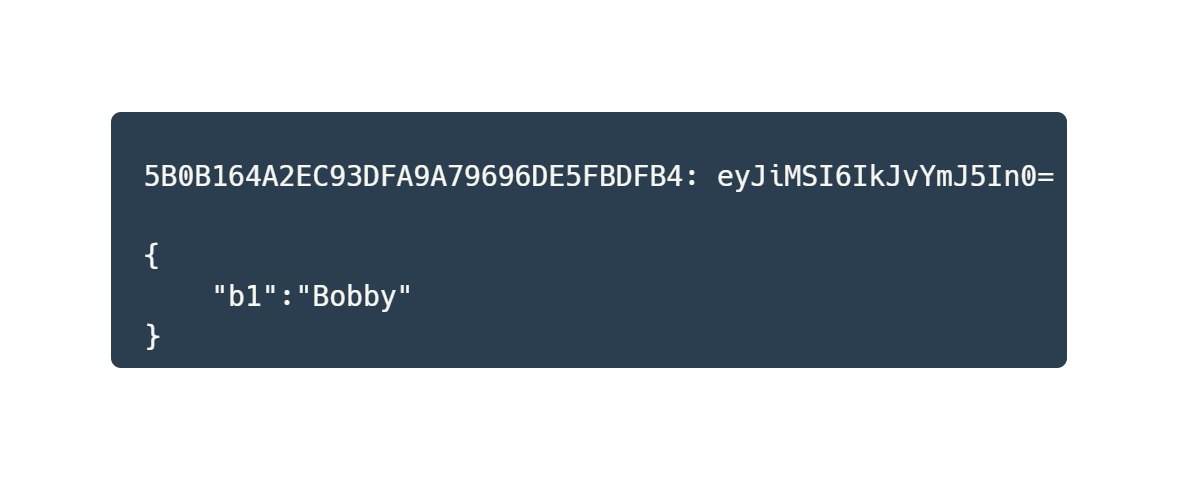
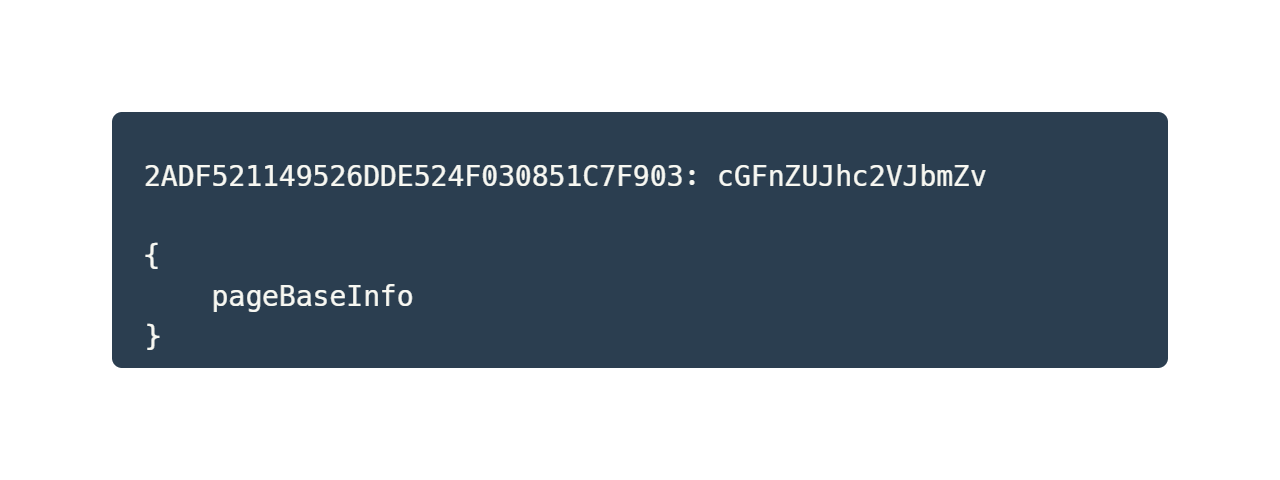
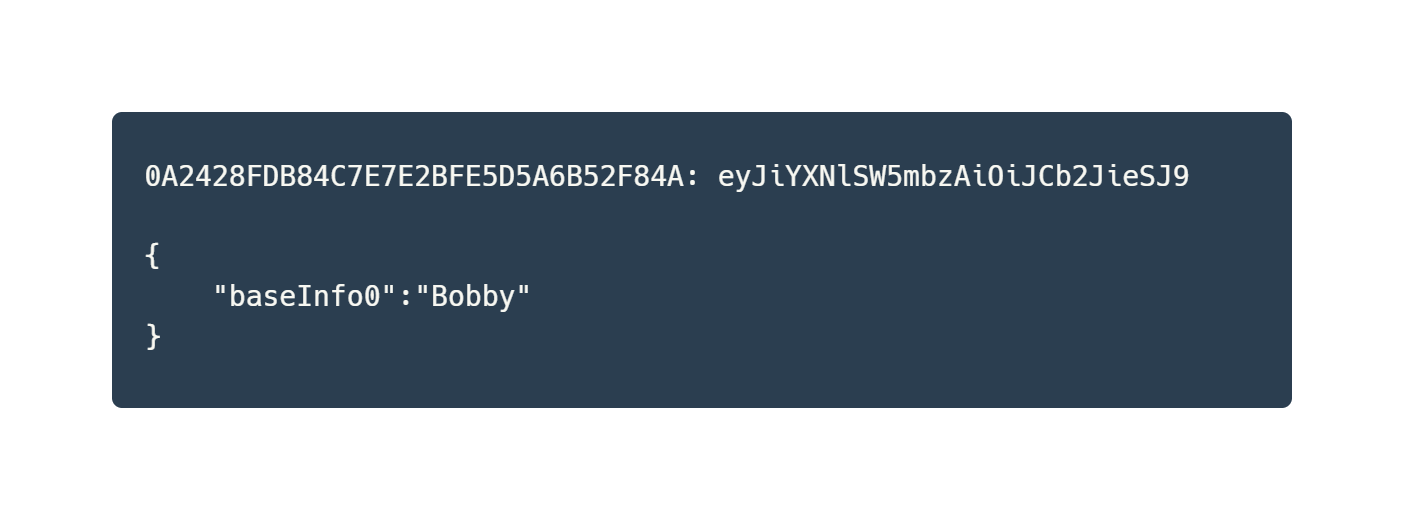
Once the user submits their “base info” – name, address, zip code, etc. – SumKit sends a post request to the endpoint
/front/dac0d37ddbcb0db4cdd4e1dc91358b9e
while passing in the victim’s token in as an argument. For instance, if we have a payload of
{
"b1":"Bobby Mildew",
"b2":"123",
"b3":"Margaritaville",
"b4":"Berlin",
"b5":"12345",
"b6":"bigmarg@gmail.com",
"b7":"1234567890"
}
it will be encoded to Base64 and sent to the endpoint as the following chunk of data:
eyJiMSI6IkJvYmJ5IE1pbGRldyIsImIyIjoiMTIzIiwiYjMiOiJNYXJnYXJpdGF2aWxsZSIsImI0IjoiQmVybGluIiwiYjUiOiIxMjM0NSIsImI2IjoiYmlnbWFyZ0BnbWFpbC5jb20iLCJiNyI6IjEyMzQ1Njc4OTAifQ==
SumKit's Websockets
SumKit relies entirely on websockets to establish a connection for sending the victim’s credit card data, along with its corresponding data from the base info page. The websocket endpoints is connected to via:
wss://{BASE_URL}/im/{TOKEN}
Once the initial connection is established, SumKit begins sending the following Base64 encoded chunk of data every two seconds:
eyJ0eXBlIjoiaGVhcnRiZWF0IiwiYXJnIjoiY2FyZCJ9
which decodes into
{
"type":"heartbeat",
"arg":"card"
}
this process continues for the remainder of this SumKit instance.
When the victim has filled out their credit card and pressed submit, the following chunk of data
{
"type":"sumbit_card",
"arg":
{
"b1":"Bobby Mildew",
"b2":"123",
"b3":"Margaritaville",
"b4":"Berlin",
"b5":"12345",
"b6":"bigmarg@gmail.com",
"b7":"1234567890",
"c1":"Bobby Mildew",
"c2":"4032 0363 6125 9672",
"c3":"10/28",
"c4":"410"
}
}
is sent via the websocket, encoded in Base64
eyJ0eXBlIjoic3VtYml0X2NhcmQiLCJhcmciOnsiYjEiOiJCb2JieSBNaWxkZXciLCJiMiI6IjEyMyIsImIzIjoiTWFyZ2FyaXRhdmlsbGUiLCJiNCI6IkJlcmxpbiIsImI1IjoiMTIzNDUiLCJiNiI6ImJpZ21hcmdAZ21haWwuY29tIiwiYjciOiIxMjM0NTY3ODkwIiwiYzEiOiJCb2JieSBNaWxkZXciLCJjMiI6IjQwMzIgMDM2MyA2MTI1IDk2NzIiLCJjMyI6IjEwLzI4IiwiYzQiOiI0MTAifX0=
Upon receiving this data, SumKit’s server responds with data to be relayed to the victim. For instance, the error
{
"error":"Sorry, the current bank payment is not supported at the monent. Please change to another bank abd try again."
}
is received as a Base64 encoded string and displayed as an error to the victim, prompting them to enter another card.
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣤⣶⣶⣶⠿⡿⢶⣶⣶⣶⣤⣄⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣠⡄⠀⠀⠀⢀⣠⣴⣿⠿⠛⠉⠁⠀⠀⠀⠀⠀⠀⠉⠙⠻⢿⣷⣦⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠰⣿⣿⣷⣶⣶⣿⠟⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠻⣿⣧⡉⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢿⣿⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⢻⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢿⣿⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣾⡿⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⠀⠀⠀⠈⢿⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⠇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣸⣿⣿⣿⡄⠀⢀⣾⣿⣧⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⠻⡿⠛⠁⢀⣾⣿⡛⣿⣿⣶⣤⣤⣤⣶⣿⣦ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⣾⣿⠟⠰⢠⢉⠹⡙⢋⠹⣩⣿⣿ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣴⣿⡿⢛⠡⢊⡑⠢⢌⠢⡑⢌⣲⣿⣿⠋ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⢿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣦⣅⣊⡔⣨⢱⣌⣦⣽⣿⡿⠛⠁⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠻⣿⣦⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣹⣿⡿⠿⠿⠿⠿⠟⠛⠋⠁⠀⠀⠀⠀ ⣠⣤⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣀⣀⣹⣿⣿⣶⣤⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢰⣿⣏⡁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⣿⣿⣿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣠⣶⣿⣿⣿⣿⣿⠿⠿⠿⢿⣿⠏⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠸⣿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⣿⣿⡍⠻⣿⣶⣄⡀⠀⠀⣀⣠⣴⣾⣿⠿⠟⠛⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠿⣿⣦⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⣿⣿⣿⣦⡀⠙⠻⠿⢿⣿⠿⠛⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣤⣤⣤⣤⣤⣤⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⢿⣿⣆⠀⠀⠀⠀⠀⠀⠀⠀ ⠿⣿⡍⠻⣿⣦⣄⠀⠀⠁⠀⠀⢀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣀⣴⣶⣿⠿⠟⠛⠉⠋⠛⠛⠿⣿⣶⣄⠀⠀⠀⠀⠀⠀⠀⠀⠹⣿⣦⠀⠀⠀⠀⠀⠀⠀ ⠀⣿⣷⡀⠈⠛⢿⡿⠂⠀⠀⠀⢸⣿⣿⣿⣷⣶⣶⣶⣿⣿⣿⡿⠟⠛⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣦⠀⠀⠀⠀⠀⠀⠀⠀⠹⣿⡆⠀⠀⠀⠀⠀⠀ ⠀⠸⣿⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⣄⡀⠈⠁⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⣇⠀⠀⠀⠀⠀⠀⠀⠀⣿⣇⠀⠀⠀⠀⠀⠀ ⠀⠀⢸⣿⣇⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⣿⢿⣿⣿⣿⣿⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣻⣿⡄⠀⠀⠀⠀⠀⠀⠀⣹⣯⠀⠀⠀⠀⠀⠀ ⠀⠀⠈⢿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⡏⠇⠀⠀⠀⠀⠀⠀⠀⣽⡷⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠈⣿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠹⣿⣿⣿⣿⣿⣿⠇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣾⡿⠃⠀⠀⠀⠀⠀⠀⠀⢀⣿⡇⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠹⣿⣧⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣶⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⣾⣿⠟⠁⠀⠀⠀⠀⠀⠀⠀⢀⣾⣿⠇⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠘⢿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⠻⢿⣿⣶⣶⣤⣤⣤⣤⣤⣶⣶⣿⡿⠟⠋⠁⠀⠀⠀⠀⠀⠀⠀⠀⣠⣿⡿⠃⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠈⠛⣿⣷⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠉⠉⠉⠉⠉⠉⠉⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⣠⣴⣿⡿⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⠻⢿⣷⣦⣤⣄⣀⣀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣀⣀⣤⣴⣶⣿⡿⠿⠛⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠉⠙⠛⠛⠿⠿⠿⠿⢿⡿⣿⣿⣿⢿⣿⡿⣿⡿⣿⢿⠿⠿⠿⠛⠛⠛⠋⠉⠁⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀

 (C:)
(C:) phishing campaigns
phishing campaigns Jennie007Greene
Jennie007Greene